In the course of doing the first-time setup on the client VM, I noticed that even though a DHCP server is running on the virtual network to which the client is attached, it was still getting a APIPA address.
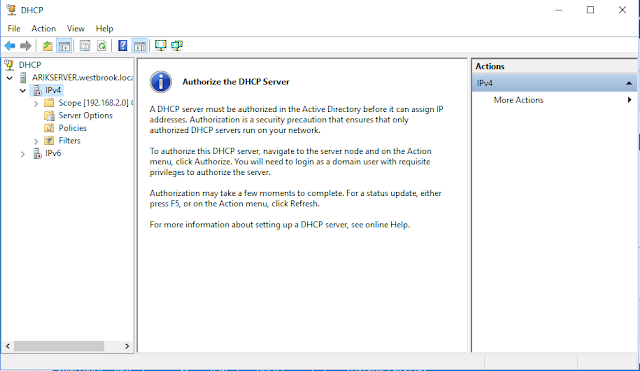
So, to begin the investigation, I opened my server VM and navigated to the DHCP tab of Server Manager. Then, I right-clicked on my server name, and opened the DHCP Manager. I noticed that both IPv4 and IPv6 scopes showed "down" icons, and when I clicked on IPv4, I saw this message.
As the message informs us, Active Directory requires DHCP servers to be authorized by an AD administrator before it will allow the server to manage IP addresses. This helps prevent scenarios where a rogue DHCP server (whether on a user's home router they brought in, or one set up for a purposeful attack) grants addresses to clients, causing widespread network difficulties.
All we need to do to authorize this server to act as a DHCP server for the Active Directory forest is to right-click on the server in the left pane of DHCP Manager, then click "Authorize" in the context menu. (If I had not been logged in as an AD administrator, I would have been prompted to enter my credentials.)
This change isn't instant; for a minute or so, the scopes remained in the "down" state. I hit F5 to refresh the window, and was relieved to find that the DHCP server was again working.
I returned to the client VM, and found that in the few seconds it took to switch windows it had already acquired an IP address in the range served by my DHCP server. It works!




No comments:
Post a Comment