First, open the Add Roles and Features Wizard. Check the box for "Active Directory Domain Services."
Once that box is checked, the wizard will let you know that several additional features are required to be installed as part of setting up AD DS. Observe this message, then click "Add Features."
On the Features page, we can see that the features indicated in the previous message are checked; in this screenshot, you can see "Group Policy Management" is checked. Click "Next."
The wizard now describes the uses of AD DS, and indicates that a DNS server must be running on the network for AD to work. I set this up in a previous post, so we will not need to do so now; however, as the wizard states, if no DNS server is available, it will automatically walk you through setting one up on the server. Click "Next."
Confirm that the selections to be installed are correct, then click "Install."
Once the installation completes, a new tab will appear in the left pane of Server Manager, labelled "AD DS". Click this tab.
We can now see that the AD DS services are available on this server. However, notice that there is a yellow alert triangle in the top bar of Server Manager (a warning message also appears above the server name). Click the alert triangle/flag icon to view the alert.
Though we have installed the AD DS services on this server, we have still not set it up as a domain controller. Click "Promote this server to a domain controller."
The AD DS Configuration Wizard appears. On this first screen, we have a few options, the one we should choose depending on our current environment:
- If there is an existing domain, and you are adding a new domain controller to it, select the first option.
- If you are adding a new domain to an environment that already has other domains (a forest), select the second option.
- If you are setting up the first domain in this environment, or want to create a new forest, select the third option.
In this post, I am setting up a whole new forest, so I will select that option and enter my root domain name. Complete this screen, then click "Next."
Since I'm creating a new forest and domain, the wizard asks me to choose the functional levels for each. In an environment with other existing clients or servers, you should choose the option that most closely matches the functional level of the existing environment - if your forest uses the Windows Server 2016 functional level, you will only be able to add domain controllers running Windows Server 2016, while if the forest uses Windows Server 2003 functional level, any version of Windows Server newer than 2003 will work.
Since there is only one server in my environment, I'll use Windows Server 2016 to get all of the newest functionality.
The other options on this screen relate to whether or not it should be a DNS server (it is), whether it should hold the Global Catalog, and whether it should be a Read Only Domain Controller (RODC).
The Global Catalog holds a partial copy of all of the AD objects that exist across all of the domain controllers in this domain, which makes searching for objects faster as it avoids needing to query several servers to find things.
A Read Only Domain Controller, as its name suggests, holds a read-only copy of the AD database. This is useful in particular for remote site environments, where it may be more difficult to ensure physical security, and where network bandwidth may be less impressive compared to the main site. As it is read-only, even with physical access an intruder will not be able to make changes that affect the local site or the rest of the domain. Because it allows users to authenticate to a domain controller at their local site, rather than having to do so across a potentially slow link to a DC at the main site, a RODC improves login times.
The final thing to do on this screen is to set a Directory Services Restore Mode (DSRM) password. DSRM is like Safe Mode for Active Directory, and can be used to repair the AD database in case of corruption. Be sure to set this to something secure, and make sure not to forget it.
Complete this screen, then click "Next."
The wizard warns us that it is unable to create a delegation for this DNS server in its authoritative parent zone because such a parent zone cannot be found. According to this page from Microsoft, this is both very common in this VM configuration and not a problem (as, for demonstration purposes, we don't care about authentication from the internet or other domains), so make a mental note and click "OK."
The next screen asks you to set the NetBIOS name for the new domain. Most likely, you should use something similar to the root domain name you entered previously. Enter the NetBIOS domain name, then click "Next."
This screen allows you to choose where AD DS will store its database files, log files, and its SYSVOL share. The AD database contains all of the objects that are part of the domain, the log files are obviously log files, and the SYSVOL share contains scripts and other files that actually implement Group Policy and other management tasks. If you wish, change the default location for each of these, then click "Next."
Finally, we reach the summary screen for the AD DS wizard. Scroll through the text box to confirm that everything is as you desire. If you would like, you can export the script that the wizard will use to create the domain to a PowerShell file so that you can more easily set up more identical instances by clicking "View script." Click "Next."
The wizard will run a check to make sure that your server is healthy and has all of its prerequisites met before beginning the installation. Since we're using the Windows Server 2016 functional level, the wizard warns us that default security settings will prevent weak security algorithms from creating secure sessions, and provides a link to a KB article with more information.
Another message, a repeat of the DNS delegation warning, can be ignored.
As the wizard warns, after the installation is complete, the server will need to reboot. If all of the prerequisite checks pass, and you are ready to reboot the server, click "Install."
Once the installation nears its end, you will see a message warning that you are about to be signed out. Click "Close." You will be signed out, then the server will reboot.
Once the server comes back up, you may see the message "Please wait for the gpsvc" for several minutes as AD and the Group Policy services initialize themselves for the first time.
Finally, once the installation and configuration completes, you will see the Windows Server 2016 login screen. Note that the username now has the domain's NetBIOS name prepended, as the server is now a member of the domain we've just created. Log in to the server, then wait for Server Manager to open.
Back on the AD DS tab of Server Manager, right-click on the server. As you can see in this screenshot, we now have a multitude of options related to Active Directory. The installation is complete, but we'll still want to create at least one user account so that we can actually work with the domain. Click "Active Directory Users and Computers".
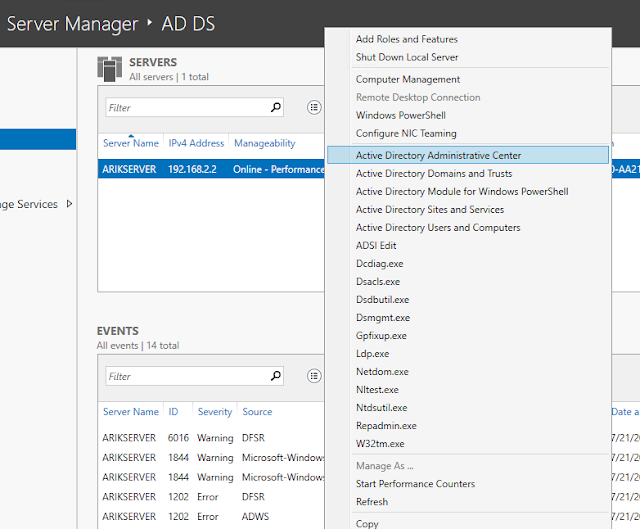
Right-click on "Users", then click on "New > User".
Fill out the form with the new user's information (I'm using my own in this case), then click "Next."
Here, you can set a password for the new user. If you are creating this account for someone else, you can give it something simple like "Password1" and check the top box labelled "User must change password at next logon." Enter a password, select any applicable options, then click "Next."
Confirm that the details are correct, then click "Finish."
In this case, I want to add my newly-created AD account to the Domain Admins group. Right-click on the account, then click "Add to a group..."
Enter the name of the group you wish to add this user to, then click "Check Names." If the name is correct, it will be underlined; if it is close, the wizard will try to guess the correct name; if it is not close to being correct, the wizard will allow you to browse to select the correct group. Once you have a group name underlined, click "OK."
A message will appear to confirm that the user has been added to the group. Click "OK." You now have a domain administrator account that you can use to join clients to the domain, etc.
You may wish to check the DNS Manager to see if a forward lookup zone called "_msdcs.<your domain>" was created. If it was not, create it manually (as a top-level forward lookup zone, not under <your domain>). Then, open Command Prompt and run "net stop netlogon" then "net start netlogon" to create the necessary DNS records. If these are not created automatically or manually, no clients will be able to join to the domain.

























No comments:
Post a Comment